MikroTik mAP Lite – phishing – smallest credential harvester
This article was made to increase awareness of Internet security. This information is for educational purposes only!
Lately MikroTik released a brand new, small-form AP. We are talking of course about mAP Lite (RBmAPL-2nD). This is really interesting product due to its small dimensions (48x49x11), low power consumption and great features for the price. It arrives to you in a package which does not help to predict the size of a mAP. Take a look for yourself:

I was interested in this product, because it seemed to me to be ideal for creating a AP meshed network for good prize… and some more. You can power it up with powerbank, PoE or even with your smartphone. Here are some photos about it’s power consumption:
I am not going to focus on multiple functionalities or advanced configuration scenarios. As soon as I bought this mAP I thought about powering it up with powerbank and making a credential harvester for a purpose! It has all what it needs – WWW server, wrtiting log files, running Virtual Machines.. (Metarouter – worth looking!) and advanced firewall. This is all what you need for PoC – credential harvester.
System I present collects logins as a proof of loosing the data by user. This is done only for statistics. People who are aware of IT security are not going to get busted – that’s for sure, but they are not a campaign target. 2FA – does the job as well. This scenario can easily be used to collect login and password for a certain account. People reaching for the free hotspot might be unpredictable…
I won’t give you full config. This is a PoC. I will try to explain that device does after unpacking and what it can do when configured properly. This can be dangerous if used by wrong hands…
Just after unpacking and powering up device propagates “MikroTik-XXXXXX” network (with part of our MAC address). mAP Lite can work as a wifi router with cable uplink, wifi router in wisp mode, repeater, hotspot system, and lots more. Take a look at: documentation. Complying the project requirements we won’t need an Internet connection for our device. If you want to collect data with other server – you can do it easily. Connect to public wifi, create virtual AP working as a honeypot – and you are done. I will describe solution where MikroTik does not have a uplink at all.
Let’s clear default configuration, rename the device, secure it with pasword and disable potentially unwanted services. As soon as we start hotspot service on our mAP and basic configuration we should be able to detect our network, connect to it and be redirected to default login template.
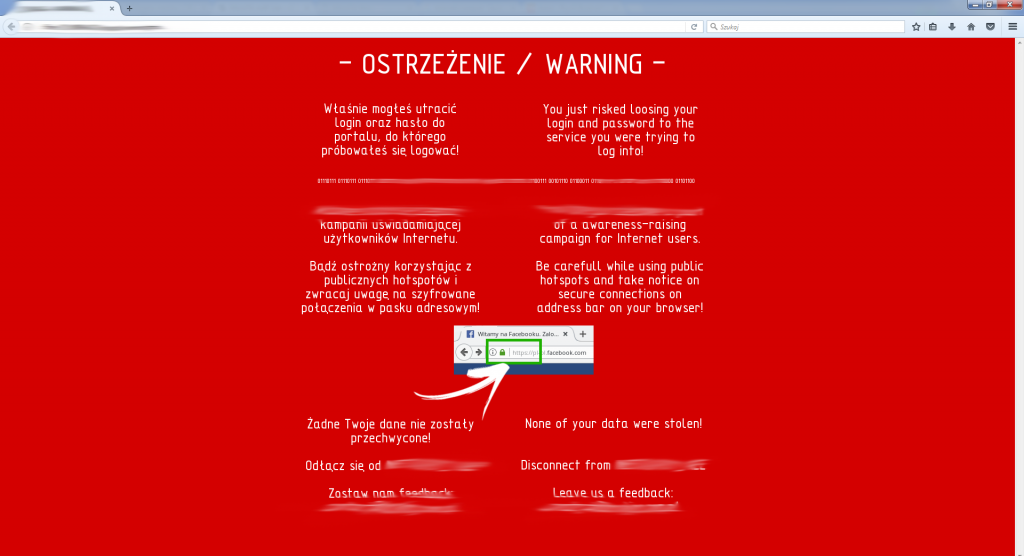
We are going to work harder – let’s create more professional looking login website which relates to place where we plant fake AP, contains logo of a well known network operator. These details make it more efficient for unaware users. Moreover we are going to clone two most popular social media network portals which are we going to use for credentail stealing.
Another step is to configure DHCP and DNS server in a way that any http traffic was redirected to IP of a fake website. Forcing a 53/UDP traffic makes us to force users with static DNS configuration.
Ready, set, go.
Client who does not take a notice of a lack of a secure connection will be redirected to this campaign website:
Due to dimensions of the device the wifi coverage area is not astonishing. You can easily cover a coffee bar, whole train car or quite big area outside though.
During next week I am going to plant some fake AP’s around the city. Two quick train-trips, shopping centre vist and a bus trip were enough to ‘catch’ 7 people beeing too eager to surf. I hope that seeing that warning website would make them more aware in the future…